Ecommerce Security: Everything You Need to Know
If you click to purchase a product or service based on our independent recommendations and impartial reviews, we may receive a commission. Learn more
If you own an online store, then you already know that staying on top of your website security is an integral part of managing your ecommerce site. While security is important for everyone online, it’s particularly crucial for ecommerce store owners who are responsible for others as well as themselves.
If you feel that managing your store’s online security is a little intimidating, don’t worry. We’ll talk you through what security for ecommerce websites is, why it’s important, the main threats facing your ecommerce store, and how you can begin to protect yourself and your online store.
What Is Ecommerce Security?
Just as you would secure a website to protect it from malicious activity, online stores also need protection – even more so, because they handle payment details, logins, addresses, and may fall victim to fraud more than a non-ecommerce site.
Ecommerce security is simply protecting your online store, its assets, and your customers’ data from unauthorized access, theft, and damage.
This includes protecting all sensitive information including credit card numbers, names, and addresses.
It should be a top priority before, during, and after the building of your ecommerce website.
Why Is Ecommerce Security Important?
There are many reasons why ecommerce security is important. They generally fall under these categories:
Protecting Customer Data: Customers trust online stores with credit card numbers, addresses, contacts, photographs, and other personal information. If this data is breached, it can lead to financial loss, identity theft, and damage to your reputation.
Legal Consequences: Ecommerce stores that do not take security seriously may face legal consequences and be held liable.
Financial Loss: You can lose a lot of money, and not just from people stealing it. Investigations, legal fees, and customer compensation cost money, especially if your insurance denies coverage because of neglect.
Damage to Reputation: With a security breach, it can be hard or impossible to regain customer trust. Would you stay with a company that breached your data?
You’re also open to things you might not have thought about, such as the news reporting on you and your data breach – like the story below reporting on GoDaddy’s three-year breach – or horrible people holding you or your business to ransom unless you meet their demands.
The Main Ecommerce Security Threats
Here are five of the most common security threats:
Phishing Attacks
We all get fake websites, emails, text messages or posts, and DMs on social media that try to get you to answer questions, or take an action like click on a link. These phishing scams try to trick you into accidentally entering personal information or downloading malware.
Phishing attacks can lead to financial loss and identity theft. They can damage your credit rating too.
There are a few ways to identify this attack. First, treat any link people post to you with a hint of suspicion. Channel your inner Benoit Blanc and investigate. Ask:
- Is this a legit website? Open a new tab and Google it – don’t follow any links in the original message.
- Is that email address format the official one? Typos in the address are a dead giveaway!
- Have you done a reverse search on that phone number?
Always be cautious of unsolicited emails or messages, especially those asking for personal information.
Malware
Malware is software designed to damage or gain unauthorized access to a computer system. Malware can be delivered through email attachments, links, or infected or dodgy websites and their “customer support.”
Malware can crash your servers and take your website offline indefinitely. You get the financial loss and liability plus you might be forced to spend a ton of money fixing the problems.
If you want to identify malware attacks, use antivirus software to detect and neutralize it. The software should be excellent quality and updated as often as needed. Many of the best ecommerce website builders come with layers of security built-in to help protect against attacks – and you can also install extra apps for added peace of mind.
Sometimes attackers will try to trick you into installing malware yourself, via phishing, so always be cautious of emails, links, or websites.
SQL Injection Attack
SQL injection attacks are next-level. A hacker finds a vulnerability in a website’s code (usually in input fields and search boxes) then injects their own SQL commands into the website’s database to access sensitive data.
They can exploit your customers’ information (opening you up to those legal and financial liabilities) or manipulate your database to alter or delete data (which can destroy your business).
Identifying an SQL requires some technical know-how. Regularly scan your website for vulnerabilities and patch any identified issues. Use prepared statements to prevent SQL injection attacks.
Cross-Site Scripting (XSS) Attacks
These are similar to SQL, but while SQL attacks a server, an XSS attacks people who use the website. XSS injects malicious code into a website, which then kicks in and works in the user’s browser.
The attacker then steals sensitive information, such as login credentials or credit card numbers from unsuspecting users. The attacker can use this information to make fraudulent purchases or sell it on the dark web to other malicious actors. Yikes!
As with the SQL you might want to leave identification up to the experts. But if you’re a bit of a techie, regularly scan your website for vulnerabilities and patch any identified issues. Use input validation to prevent XSS attacks.
DDoS Attacks
DDoS stands for “Distributed Denial of Service,” and it floods a website’s server with so much traffic that it can’t handle the load and crashes. Like when the doors to Walmart open Black Friday.
A DDoS attack can be a major headache. It can cause the site to crash and be unavailable for hours, or days, which means customers can’t make purchases or access their accounts. You lose money and customers flee pretty fast. If your store is down for too long, your search engine rankings can tank.
To spot a DDoS, use a DDoS protection service to detect and prevent attacks. If you monitor your website’s traffic, you’ll be able to respond promptly to any unusual activity. Many of the best ecommerce hosting providers come with DDoS protection built-in so that you don’t have to deal with it on your own.
Ransomware Attacks
A ransomware attack is where a cyber criminal is able to access a website’s data and hold it hostage.
The attacker will usually threaten to block access to, delete, corrupt, or publish the data unless the victim pays a ransom fee.
The most common way for a ransomware attack to take place is via phishing emails where users will unknowingly download malware that infects their device and looks for files to encrypt and “hold hostage”.
By ensuring you regularly backup your files you can regain access quickly if you’re under attack.
The FBI recommends that victims do not pay the ransoms to attackers and should instead report attacks to the authorities. Remember, cyber criminals are hardly trustworthy and just because you pay the ransom doesn’t guarantee you’ll get your files back.
One of the biggest ransomware attacks in recent years was when Colonial Pipeline fell victim to ransomware attackers, leaving Americans living in the Southeast states facing gas shortages and leading to President Biden issuing emergency declarations.
While a ransomware attack on your website may not result in Presidential action, it could still be catastrophic for your business.
API Attacks
API stands for Application Programming Interfaces and these are crucial for seamless communication between multiple applications and systems.
Basically, an API allows two different systems to communicate with each other, for example, when you send a mobile payment or order an Uber on your mobile phone, you’re using an API.
The app or system on your mobile connects to the internet and sends the information to the server (e.g. your Uber booking, where you are, and where you want to go), the server receives the data, interprets it, and performs the necessary action (e.g. finds you Uber drivers nearby) and then sends the data back to your app/phone, that will then interpret the data from the system and present you with the information (e.g. your driver is 5 minutes away).
An API attack therefore is where an API is used maliciously to breach communications, access data, and manipulate commerce situations.
The best way to prevent API attacks is to ensure all data is verified, filtered, and then deleted when no longer needed.
IoT Attacks
The Internet of Things (IoT) is the linking of devices via the internet, for example smart home hubs, smart TVs, fitness trackers, smart washing machines, and even smart cars (no, not the brand of famously small cars but cars that use connected data to optimize performance).
Most brands use IoT too, including for fleet management or to manage a supply chain.
IoT software and devices can be vulnerable to attacks such as data theft, phishing, and DDoS attacks.
Thanks to default passwords, unsecure communications, and the increased use of automation and AI, hackers can infiltrate IoT systems.
If you rely heavily on IoT systems for your business (or even if you’re just dipping your toe into the process) you need to ensure you are constantly running tests to check for any vulnerabilities in your systems.
Ecommerce Security Best Practices
There are best practices for security for ecommerce websites, and it will help you to know them.
But bear in mind doing all these yourself untrained is not as secure as a professional doing this for you. In fact, 95% of cyber breaches come from simple human error. But most people can’t afford to keep a security team on staff 24/7, so this is at least a good start.
1. Use Secure Passwords
Let’s face it, we’ve all been a little lazy at some point or another with our passwords. That should stop. We know they’re really important and it’s so easy to sort it out!
Passwords should be at least 12 characters long, and a mix of uppercase and lowercase letters, numbers, and symbols. You can use a password manager to generate and store secure passwords. Use two-factor authentication (2FA) for added security.
2. Implement SSL/TLS
SSL/TLS is a security protocol that encrypts data transmitted between a web server and a user’s browser. It’s very important because implementing SSL/TLS ensures that customer data is secure when transmitted over the internet.
It’s not the most difficult thing to do, but it’s not for straight-up beginners either and takes a little time. Get an SSL/TLS certificate from a trusted certificate authority (CA). Install the certificate on your web server. Use HTTPS for your website.
Find Out More
- Most good web hosts come with basic SSL certificates automatically – check out our list of the Best Free SSL Hosting Providers for our top picks.
3. Regularly Update Software
It’s no shock that updating your ecommerce store’s software is extremely vital. Regularly updating your software, including your operating system, web server, and ecommerce platform, can patch security vulnerabilities and prevent security breaches.
It’s fairly easy to do (though the specifics will range from software package to software package). Enable automatic updates for your software, and regularly check for updates and install them promptly.
Find Out More
WordPress sites can be prone to attacks when you forget to keep up with software, theme, and plugin updates. Our full guide on How To Secure a WordPress Website gets into the specifics of how to keep your WordPress site safe.
4. Use Both Antivirus Software and Firewall Protection
These are both absolutely necessary. Antivirus software stops viruses from harming your system and a firewall is a security measure that monitors and controls network traffic to prevent unauthorized access to your system.
In both cases, make sure you have the best software you can afford – not all brands are created equal! Good antivirus software should include malware detection, email scanning, and web protection.
It’s not too hard to install anti-virus software or implement a firewall on your web server. Configure the firewall correctly: Set up the firewall to block unauthorized traffic and only allow traffic that is necessary for your business operations. This includes setting up rules to block traffic from suspicious IP addresses, limit access to specific ports, and restrict traffic to authorized users.
Make sure they’re always updated. Also run regular scans – don’t just wait for the updates because things can slip through before developers are aware they exist.
5. Back Up Your Data and Monitor Your Site
It’s important and easy. Back up your data for a quick recovery from a security breach or system failure. Regularly monitoring your website traffic can detect unusual activity and prevent security breaches.
Use a backup service or software, which makes it all so easy. Store your backups offsite, in a secure location. Use a website monitoring service or software to monitor your website traffic. You can set up alerts for unusual activity.
6. Implement Two Factor Authentication
Two factor authentication is the process of a user being admitted into a website or application after they have submitted two pieces of “evidence” to confirm their identity. The most common pieces of evidence required are a password followed by a code, usually sent to the mobile number on file for that user.
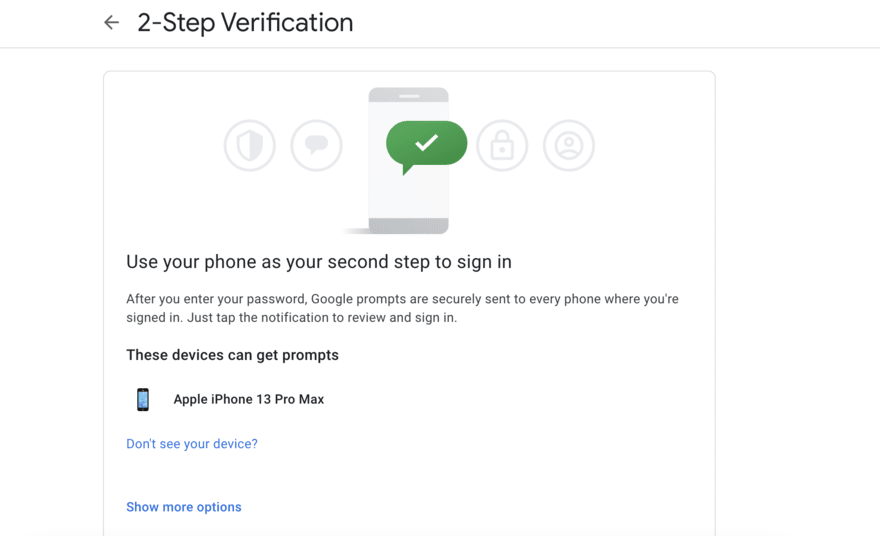
2FA verifies that the user trying to access the account is in fact the owner of the account and not just someone who knows the password.
Often during a data breach or attack usernames and passwords can be stolen, but the additional factor keeps the account safe as it will usually be something that can only belong to, or be accessed by, the account holder.
7. Conduct Regular Security Assessments
Security assessments use a variety of techniques to conduct an in-depth audit of your ecommerce store’s defence measures for both external and internal attacks.
The main goal of a security assessment is to highlight any vulnerabilities in your website or system, allowing you to spot them and fix them before an intruder does.
There are various online tools you can use to run a complete security assessment on your website. Remember, if a tool can find the vulnerability, so can a hacker.
It’s important to run regular security assessments to ensure you are dealing with any issues as soon as they arise and not leaving your website open to an attack.
8. Implement a Security Incident Response Plan
A security incident response plan is a detailed, written plan, usually with six key phases, that help your internal IT team and staff deal with any type of security breach or attack.
Your security incident response plan should include:
- Preparation – this includes training your staff on security policies and their roles and responsibilities in the event of an attack.
- Identification – who will be responsible for identifying the attack? How will it be identified and communicated?
- Containment – be clear on how you will contain the breach to ensure minimal impact to your business.
- Eradication – how will you solve the problem and rid your servers of the threat?
- Recovery – the process of returning your systems back to normal.
- Lessons learned – how will you evaluate your response to the attack and determine what you can learn from it for the future?
Conclusion
Of course we don’t like to be reminded that nasty things can happen to the business we’re passionate about. But owners of ecommerce stores must implement these best practices to protect against threats in ecommerce security for websites.
It doesn’t matter how small your business is – why take the risk when you don’t need to? Familiarize yourself with these solutions and you’ll be on your way to making your ecommerce store more secure for the future.


Leave a comment